The Definitive Guide to cross border payment
The Definitive Guide to cross border payment
Blog Article
Nowadays, carders and fraudsters can Fortunately obtain and sell magstripe card data with a relatively high degree of confidence that it will be usable, mainly because magstripe data is all static. EMV card transactions, on the other hand, incorporate dynamic data. Banks generate one-time codes for every transaction, so any stolen transaction data may perhaps only be legitimate for a single minute or a lot less.
This technique is way from gambling, mainly because it requires thorough Assessment along with a deep understanding in the market. In conclusion, forex trading is not really a scam, but rather a reputable investment alternative. Like almost every other investment, it will come with challenges, and achievements requires understanding, expertise, and knowledge. By debunking popular myths and misconceptions, it will become obvious that forex trading is regulated, calls for effort and perseverance, and relies on Examination somewhat than luck. Educating oneself about the forex market and seeking highly regarded brokers may help investors navigate this investment solution properly.
Flexxon may be the business chief to build NAND flash storage gadgets. Our crucial aim is usually to innovate memory gadgets making sure data protection and reliability.
With so much activity and no centralized governing system, there is sufficient opportunity for individual traders to drop prey to your forex scam. A few are fairly typical that you should pay attention to if you choose to trade.
The breakthroughs and improvements that we uncover bring about new ways of thinking, new connections, and new industries.
Some people remedy for this by making it challenging to accessibility the account in which they regulate their Content material Policy. Having said that, this is dangerous and inhibits you from making your Articles Coverage more restrictive when essential.
It may be challenging to recognize these signal sellers as scammers, because they normally offer rave reviews and quotation a history of making substantial revenue. No matter what details they existing, beware.
bark may be the ideal decision of a parental Command app for folks that need a Instrument that will do more than only make nice marketing statements. bark is a product that has actually been thoroughly examined and trustworthy by dad and mom and educational institutions to protect about 5.
But with the X-08 and X-09 locks launched in 1999 and 2002, Davis located that his voltage leaking attack worked. Thankfully, the method was significantly harder than during the Cencon or Auditcon versions. For the reason that X-0 collection have no physically available ports, Davis experienced to eliminate the Liquid crystal display screen, attach his probes to wires that connected to that display, after which use some excess electrical engineering tips to cancel out the "noise" in the electrical signals sent to that display ahead of he was ready to read the underlying voltage leakage that reveals the combination.
Set up an software or configure the community settings on your computer systems and smartphones to place to your DNS Written content Policy so that websites are blocked even when on 4g/5g or when utilizing a WiFi link absent from your household.
This is often completed by physically accessing the gadget and manipulating it to copy the malware with the help of exterior keyboards and USB sticks. The attackers need to make the an infection persist in time, that may be achieved by changing reputable system executables or by setting autorun keys at startup time.
A 2nd generation with the Cencon locks, produced in 2009, at first presented a much more severe challenge. That version makes use of AES encryption to protect the lock's blend in memory, Davis claims, so that it cannot be browse when it's transferred for the CPU. He discovered that it was feasible to make use of another method of electrical power Assessment to extract the AES vital and decrypt The mix, but only after several readings and days of research, which wouldn't be an exceedingly realistic attack.
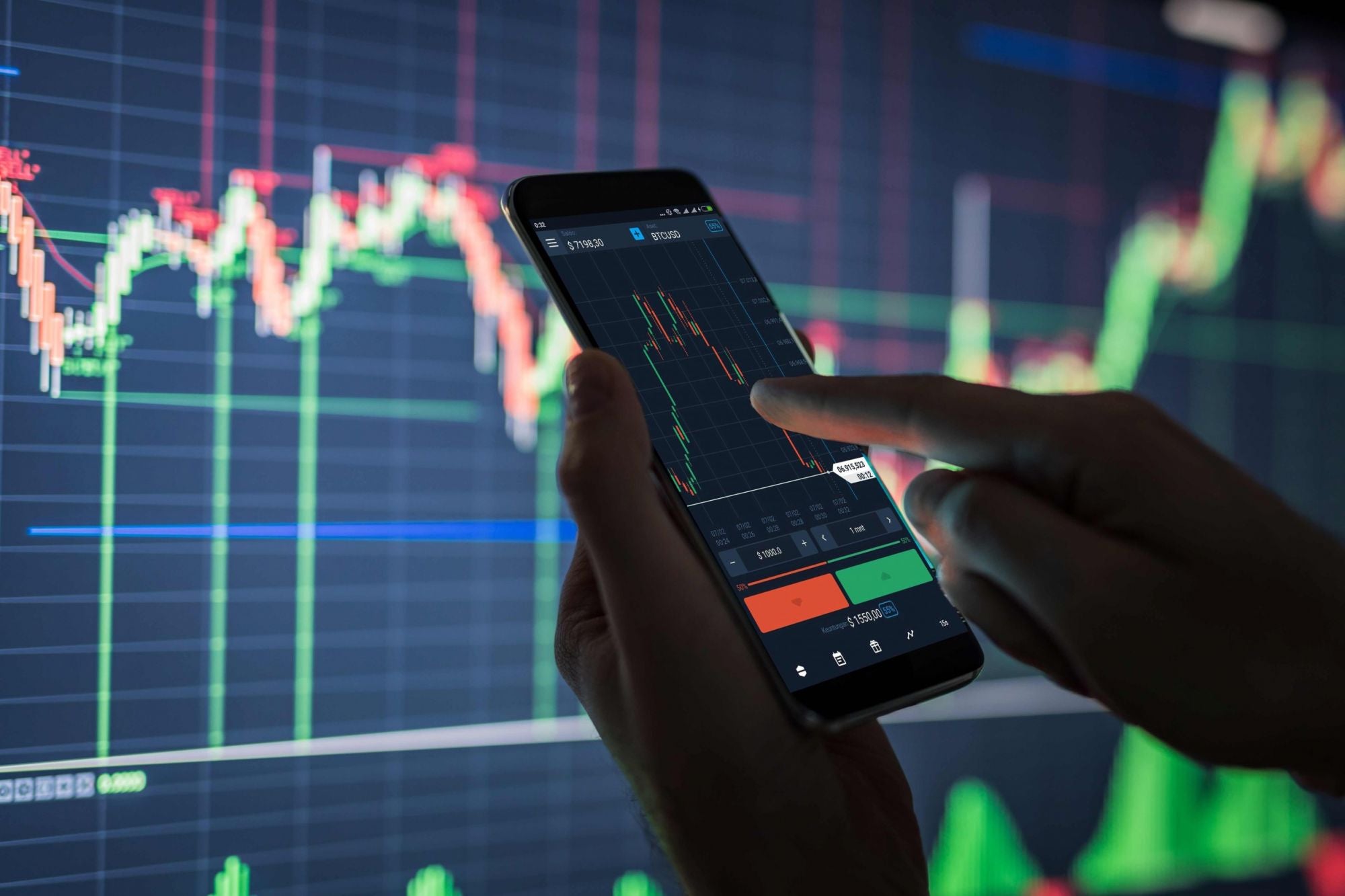
Forex trading (also typically called International Exchange, currency or FX trading) is a world market for trading a person nation’s currency in exchange for one more state's currency. It serves given that the backbone of international trade and investment: imports and exports of goods and providers; financial transactions by governments, economic establishments or individuals; global tourism and travel – these need the use of capital in the shape of swapping one anchor particular currency for a particular level of One more currency.
Be specifically careful if they begin to check with for personal data that can be utilized for things such as identity theft. If it feels unpleasant and pushy, keep away from it.
Information addresses
https://www.investopedia.com
